HackFu - The Final Wrap Up
- 25 Oct 2013
It’s been a couple of months since the awesome excitement of HackFu 2013 and we thought it would be a good time to take a look back at some of the highlights.
Not only so the attendees can relive the awesomeness but also so that anyone who didn’t get to come can see why they should try and win a place next year.
For those of you who aren’t sure what you need to do to get an invite, let’s do a quick recap of who came along. Firstly are all the MWR employees and members of our intern scheme, they get to come by default. Next up were the HackFu VIPs who are people who have given their time to help the team at MWR and have been rewarded with lifetime access to the event. Then there are the MWR alumni, the top 5 former employees as voted for by the company. There are also numerous special guests and winners of the various competitions that are held in the run-up to the event. If we don’t know you and you don’t know us, winning one of these competitions is the best way to get an invite!
This year there were two chances to win a ticket including one given away at UNCON and plenty in our online competition. There was a great response to the competition with over 150 entries from 21 countries from all around the World. The challenges were intentionally tough and when the solutions were reviewed there were a total of 10 winners. Unfortunately a couple of our winners weren’t able to attend because of commitments to their employer or better halves, but they all won an MWR goodie bag to partly make up for it. The great news was that 7 of our winners made it to the event and had flights, accommodation, food and the ability to participate in the event all provided to them by MWR.
If you had a chance to have a go at the challenge but didn’t get all the answers then take a look at this great write-up for some helpful hints and tips (spoiler alert as we will be releasing the challenges later in the year for those that didn’t enter):
So with all our competition winners and guests onboard, the teams got into the spirit of the event. This year our 4 teams were:




Aztechs
Crystal Blue Persuasion
Hackf00f
Malicious Intent
As you may have guessed from the teams, this year’s theme was the Crystal Maze and no expense was spared to make our version even better than the original. The most important part of this was the venue and this year’s was a cracker. We were very fortunate to be able to take over the RAF Air Defence Radar Museum in Norfolk for the entire event.
If you’ve never been its well worth a visit (even when HackFu isn’t there) as you will learn about the history of radar and the important role it has played in the recent history of the UK. The whole place is brought wonderfully to life by the dedicated and knowledgeable volunteers, fantastic exhibits and authentic setting. All overseen by the curator Chris who was a key part in enabling HackFu to take over the museum and transform it into the Crystal Maze. Take a look at these photos to see for yourself.
Fans on the TV show were excited to see the four zones recreated with lots of little authentic touches. Within each zone were a number of themed challenges that tested the skills of all of the competitors. To give you a flavour of the type of challenges the teams faced a summary of each zone’s challenges are included here:
Inside the Aztec zone you’d have found sunshine, tropical plants and more than a little heated competition to solve the challenges. The holiday zone of the maze was anything but that for the teams that took it on.
The Maze – The teams had to find their way round a maze of over 30 Cisco routers and switches set-up to emulate the narrow and disorientating streets of an Aztec town. They needed to break into the maze from the outside and then navigate their way to the altar of the gods using their best networking skills and Cisco command line foo. Many were lost within the maze, never to be seen again.
The FileSystem – The teams were given a file and had to work out what it was and how to access it. It turned out that it was a ZFS image containing tourist posters for the Aztec zone and the teams had to access the image correctly and then recover some deleted data.
The Idol – Rather than attempt to do justice to this awesome challenge, put together by one of the HackFu VIPs, its best to read an article written about it. If you didn’t get a chance to try this game out you missed something special as you can see here. This is a picture of the rover the teams had to use to navigate their Aztec wonderland.

If you managed to fight your way past the biohazard warnings and chunky security cameras you’d have found the teams inside the industrial zone. The whirring and clanking of the machinery didn’t appear to put anyone off as they attempted some fiendish challenges.
The Bug – It appeared that someone had hidden a bug inside a radio control tank. What the teams had to do was interface with it through its controller unit and get it to divulge its secrets. A bit of firmware analysis, use of a bus pirate and some sneaky thinking were all that was needed to defeat the agent who had bugged the maze.

The Murder – Call the police, there’s been a murder at the army base! The teams were confronted with a crime scene and a series of clues left by the murderer. Collecting fingerprints, analysing samples from the crime scene, using Software Defined Radio to listen to announcements from the base’s comms system and reconstructing elaborate QR codes used by the victim’s criminal associates were all part of the investigation.

The Hardware – In what turned out to be the most frustrating challenge for most of the teams, they were required to pull some data off an old server that had been left abandoned in the zone. The only catch was that it didn’t have a bootable hard drive, they couldn’t attach a keyboard and screwdrivers were banned. Anyone tried PXE booting a box like this? The teams found out it’s not as easy as they thought!
Inside our very own medieval fortress the teams had to compete by the light of a flickering candle. With Raymond the Raven keeping a watching eye over everyone it’s a fun yet draughty place to be. Even more fun with the fiendish puzzles within.
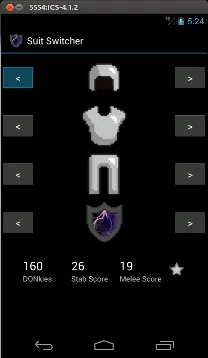
The Armoury – Every self-respecting security tester should have drozer in their armoury. In this case it was about using drozer to attack an armoury, or more accurately an online retailer selling suits of armour via their Android application. If you didn’t know how to attack Apps on Android beforehand, you certainly would do after this.
The Incident – Fans of “Choose your own Adventure” books would have loved this challenge as the format was recreated using an incident response storyline. The teams were thereby in control of their very own adventure. Read the story, choose your actions and save the day. Don’t worry if you didn’t get a chance to play along, this is now integrated into MWR’s new Advanced Attack Management Training course, contact us for more info.
The Algorithm – You’ve all played those maze games where you need to trace a path with your pencil from start to finish. Now imagine you need to get a computer to solve one using the optimal path. That was the challenge here, navigate the maze safely and the prize was yours.

Using the old control room of the museum the competitors were transported to a retro world of the future. Just like in the real crystal maze the challenges here were just a little bit harder than the others and all set in the distant future.
The Linux – This challenge was good old fashioned hacking of a Linux system. Finds the bugs, gain a foothold, escalate your access and pwn the box. It’s not all point-and-pwn you know, sometimes it takes effort to get from zero to hero.
The Moon – The challenge was quite simple, analyse a series of photos of the Moon to identify some hidden data. Then use some general knowledge (or Google) to identify objects on its surface and solve the challenge. The lesson here was that there is more than one way to analyse what’s on a piece of paper.
The Phone – The teams had to analyse an access control system that used an Android application and MiFare Classic RFID card. The idea was to analyse the structure and content of the data on the MiFare cards so that data could be skilfully replaced to attack the Android App. Who said you can’t attack the back-end systems by altering your access card?
In each zone the teams only had 5 hours to complete all of the puzzles and enter their answers into the maze’s central computer banks. This took good team-working, effective delegation and often a couple of beers to lubricate the brain cells. However, that wasn’t all that the maze had in store for them.
Within the maze were a series of RFID controlled sensor points that allowed the teams to check in and out of the zones using specially coded wristbands.

These systems also unlocked a set of fast paced mini-games that if completed would win the teams crystals and with them extra time inside the crystal dome at the end of the contest.

Swipe your wristband to start the clock and make sure you have swiped out before the time runs out otherwise it’s a lock-in. All your favourites from the original TV show were included with the well known categories of Physical, Skill, Mental and Mystery games making their expected appearance. From blowpipes in the Aztec zone to Nerf guns in Futuristic, lock-picking in Industrial and a Fairytale mystery in Medieval. Crystals were won, players were locked in and lots of fun was had by all.
The culmination of the event was the final showdown inside the crystal maze. The four teams went head to head in a capture the flag style shootout. The teams each had a VM that they had to keep online and running whilst the other teams tried to take them down. The teams traded their crystals for extra time analysing and patching up their VM. The all seeing eye of the Domebot kept the score as the teams battled for an hour in an intense and frenzied fight to the death.
We managed to capture some of the excitement of the showdown and the rest of the event in our awesome “HackFu Movie” that you will be able to see a teaser for in the near future. Want to see the full movie? Well that’s a challenge that’s left up to you. As a starter for 10 I can tell you that you won’t find it on any of MWR’s websites. However, if you’re good, or very, very lucky you may just find it lurking somewhere out there. We’ll announce the teaser on twitter when its ready.
So if you thought this year’s HackFu was enough to blow your mind then you may want to steer clear of next year’s event. HackFu 2014 promises to be bigger and better with a fresh new theme, another cool venue and even more awesome challenges and games. So if you want to experience the full force of HackFu be sure to put the date in your diary:
19:00 on 26th June to 18:00 on 28th June 2014
Location: Announced nearer the time
Keep an eye out next year for the competition as well as a number of other opportunities that could enable you to win a place at the event. Follow us on Twitter to ensure you don’t miss anything including “HackFu the Movie: 2013”.