Azure Connected Machine Agent Elevation of Privilege Vulnerability: Console Popup
-
 Sharan Patil
Sharan Patil - Published: 20 Jan 2026
- Type: Local Privilege Escalation
- Severity: High
 Sharan Patil
Sharan Patil Azure Connected Machine Agent 1.48 and 1.49
Azure Connected Machine Agent installer versions 1.48 and 1.49 were vulnerable to Elevation of Privileges via MSI repair functionality due to creation of a scheduled task which resulted in a console popup exploit. The exploitation requires GUI access.
Console popups are the “command prompt” screens sometimes seen when a software or an installer is executing some tasks. These popups could be used for local privilege escalation. However, these popups may flash only for a few milliseconds and it could be difficult to click on the prompt. An opportunistic lock could be used to improve the efficiency of catching these popups.
In our introductory blog, we briefly described the Microsoft Software Installer’s (MSI’s) repair functionality. We recommend reading the blog posts mentioned in the Introduction section to have a better understanding about MSI repair exploits. Coincidentally, an updated version of the agent, version 1.48 was released at the time we were researching and reporting other issues to MSRC. The New features and enhancements section had a note:
Introduced a scheduled task that checks for agent updates on a daily basis. Currently, the update mechanism is inactive and no changes are made to your server even if a newer agent version is available.
Investigation of this feature led to the discovery of three Local Privilege Escalation (LPE) methods, one of which is described below.
During the installation of the latest version of the agent (1.48), a console popup was observed. Using Process Monitor (procmon) to identify the process responsible for the popup did not yield a result. Assuming the popup may be present during the installation process, a reinstall was attempted. During the reinstallation, the popup appeared again due to the new feature which created a new scheduled task azcmagent. Curious if the popup would flash again when an MSI repair was initiated, Mandiant’s msi_search.ps1 script was used to identify the MSI file in the C:\Windows\Installer\ directory that belonged to Azure Connected Machine Agent. Once identified, the repair functionality was triggered using the command msiexec /fa C:\Windows\Installer\[filename].msi. After the repair functionality triggered the popup, it was investigated if a low-privileged user could also trigger the repair operation. This functionality is usually restricted to privileged users. However, the investigations indicated otherwise in this case.
Ironically, Microsoft introduced a bug while it was supposed to be a feature. The auto-upgrade feature was later implemented in the September release version 1.56.
Azure Arc installer version 1.48 created a scheduled task azcmagent to trigger every day. The installer created the scheduled task with execution time between 01:00 and 02:00 server time. Investigating the MSI with Orca confirmed that it was a CustomAction defined as shown below:
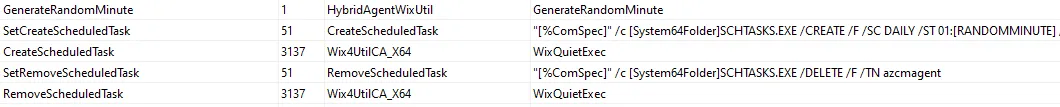
"[%ComSpec]" /c [System64Folder]SCHTASKS.EXE /CREATE /F /SC DAILY /ST 01:[RANDOMMINUTE] /TN azcmagent /TR "[System64Folder]WindowsPowerShell\v1.0\powershell.exe -File '[INSTALLFOLDER]azcmagent_check_updates.ps1'" /RU SYSTEM
While creating the scheduled task, a conhost.exe pop-up was presented for a few milliseconds. Having read Mandiant’s blog as part of the literature review, we wanted to verify if it was a similar console popup bug. To determine the installer name, msi_search.ps1 script by Mandiant was used.
Initiating the repair functionality forced the MSI installer to create a new scheduled task. The scheduled task executable schtasks.exe required the file C:\Windows\SysWOW64\en-US\schtasks.exe.mui for executing. A low-privileged user could use an opportunistic exclusive lock on that file. Once the lock was triggered, the conhost.exe popup did not terminate anymore. The extended time allowed a low-privileged user to reliably escalate their privileges.
SetOpLock.exe C:\Windows\SysWOW64\en-US\schtasks.exe.mui x
msiexec /fa C:\Windows\Installer\<filename>.msi
conhost.exe popup with the title c:\windows\SysWOW64\SCHTASKS.EXE is presented.cmd is used which opens a command prompt window as the NT AUTHORITY\SYSTEM user.The repair function should reinstall the agent successfully.
Reinstallation is successful and an elevation of privileges was observed and a command prompt as NT AUTHORITY\SYSTEM being obtained.
Update the agent to the latest version available.
| Date | Action |
|---|---|
| 22 Jan 2025 | Initial disclosure |
| 20 Feb 2025 | Vulnerability confirmed |
| 17 Mar 2025 | MSRC confirm vulnerability fixed |
| 9 Jun 2025 | Further communication with MSRC about the case status |
| 10 Jun 2025 | CVE-2025-49692 is reserved |
| 8 Jul 2025 | CVE-2025-49692 is published |