Username Disclosure Vulnerability in DBD+ Application Used by Megafeis Smart Locks
-
 Abdullah Ansari
Abdullah Ansari - Published: 4 Mar 2023
- Type: Sensitive Information Disclosure
- Severity: Low
 Abdullah Ansari
Abdullah Ansari DBD+ Mobile Companion Application for IOS & Android - IOS: Version 1.4.3, Android: 1.4.4. WithSecure leveraged this issue in a chain of vulnerabilities on Megafeis branded locks with the following model numbers: FB50S Smart Padlock, GS60FB Smart Outdoor Lock, GS40S Smart Padlock, GQ10FB Smart Bike Lock
CVE-2022-45634
An information disclosure issue was discovered which allowed an attacker within Bluetooth broadcast range of a target Megafeis-branded smartlock to acquire sensitive information. This information was the email address and phone number associated with accounts which owned Megafeis smart locks.
The username can then be combined with the API server’s password reset issue (CVE-2022-45637) or the API server’s password policy issue (CVE-2022-45635) to facilitate an attacker’s efforts take over the target user’s account.
As of this advisory’s publishing date, there has been no response from the manufacturer, nor is WithSecure aware of any remedial action taken.
Additional information on this issue, along with related issues discovered by the researcher, can be found in the following locations:
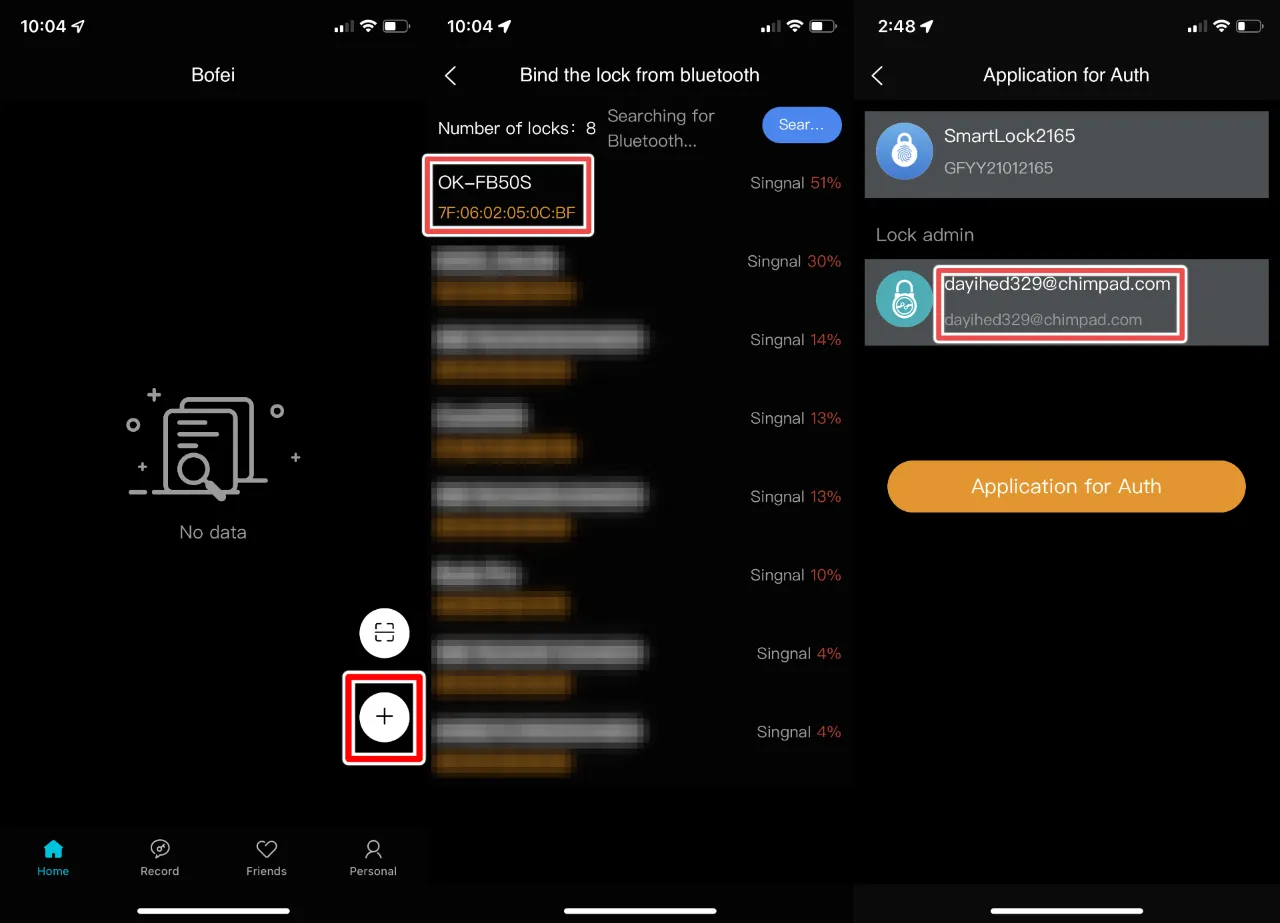
To demonstrate an attacker’s ability to expose the email or phone number associated with a Megafeis smart lock owner’s account, the following steps can be performed within version 1.4.2 of the DBD+ application:
The screenshots below illustrate these steps from the view of the mobile application and reveal the username/email address of a test user researchers created while investigating this issue:
| Date | Action |
|---|---|
| 5 Aug 2022 | WithSecure makes first attempt to notify the vendor |
| 23 Aug 2022 | After no response from the vendor, WithSecure makes a subsequent attempt to notify the vendor |
| 16 Nov 2022 | After months without response from the vendor, WithSecure notifies MITRE to Request a CVE ID |
| 31 Jan 2023 | MITRE assigns CVE ID |
| 3 Mar 2023 | WithSecure publishes this advisory |